Cross-Chain Governance
Pre-Requisite Reading
Summary
Purpose
This document describes a governable system for executing permissioned actions across chains.
We aim to clearly describe
- what contracts comprise the system for calling permissioned functions across chains
- which functions will be delegated to this system at launch, and
- (directionally) who will have permission to call these functions at launch and in the future
Out of Scope
This document does NOT describe a system for how governance actions will be proposed, voted on, and/or approved before being executed.
It does not describe how contract upgrades will be written, reviewed, verified.
Overview
We define a role, governor, with the power to perform permissioned actions across chains. In order to empower the governor, we deploy a cross-chain application comprised of a GovernanceRouter contract on each chain.
Each GovernanceRouter can be delegated control over an arbitrary set of permissioned functions on its local chain. The only way to access the permissioned functionality is to call the function via the GovernanceRouter contract.
Each GovernanceRouter is programmed to accept messages only from the governor, which is deployed on only one chain. The governor may call the contract locally (if it is deployed on the same chain), or it may send it messages remotely via Nomad. Because of its exclusive power over the GovernanceRouter contracts, the governor has exclusive rights to perform all of the permissioned roles that are delegated to the GovernanceRouter on each chain.
The system receives orders from the governor and carries out their effects across chains; it is agnostic to how the governor chooses to operate. This maintains flexibility to design the governance proposal process in the future.
At launch, the core functionality that will be delegated to the GovernanceRouter on each chain is the power to upgrade the implementation of the Home and Replica contracts. This way, the governor will have the power to conduct upgrades of the Nomad system on every chain. More details on the upgradability system can be found here.
At launch, the governor will be a multisig of trusted team and community members. In the near future, the governor role will most likely be transferred to a more fully-featured set of contracts capable of accepting proposals, tallying votes, and executing successful proposals.
Message Flow Diagram
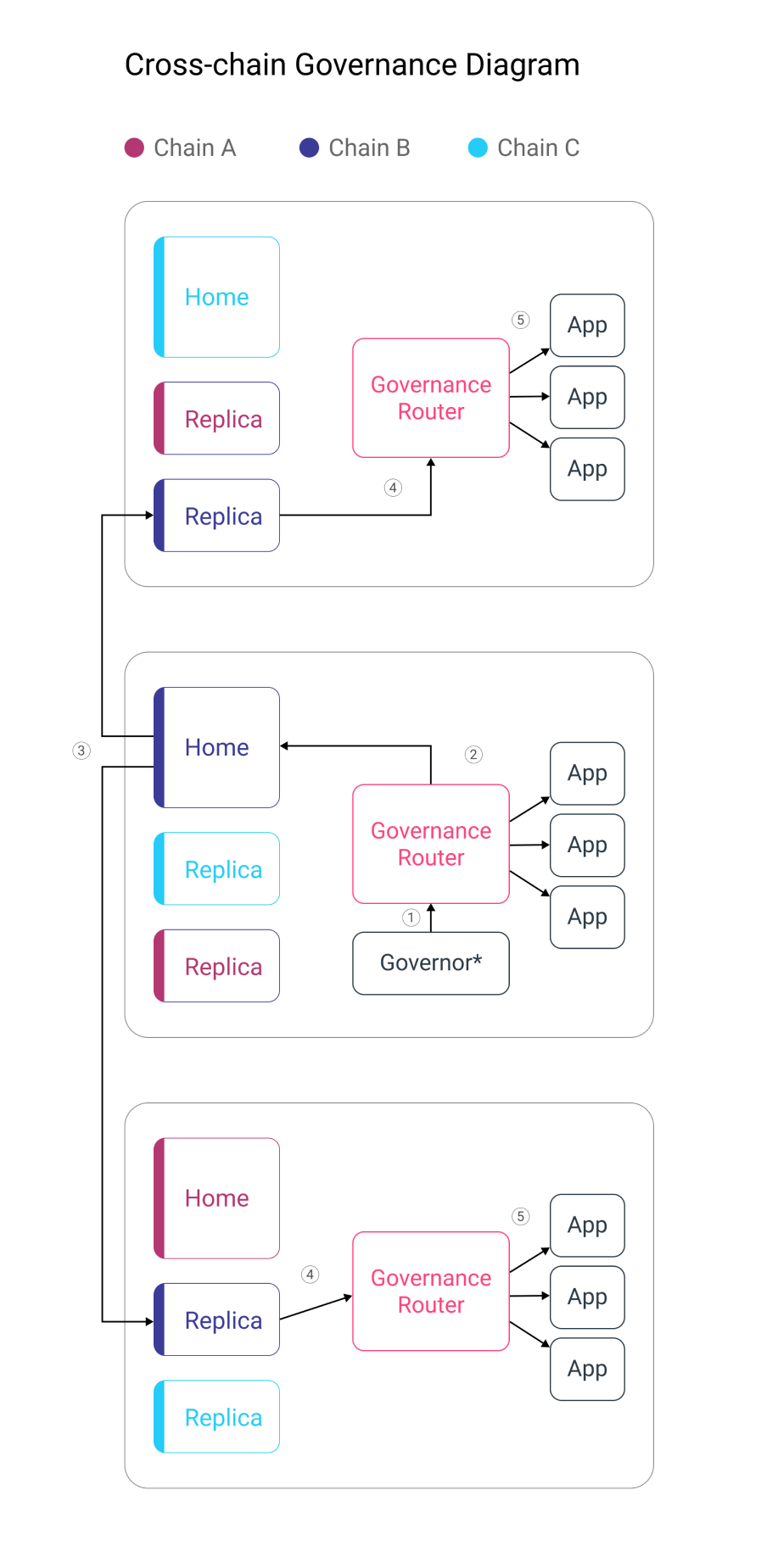
governorsends message to its localGovernanceRouterGovernanceRouterdispatches the message...- if the recipient is local, to the recipient directly (→ process finished)
- if the recipient is remote, via Nomad to the local Home contract (→ continue to 3)
- Message is relayed from local
Hometo remoteReplicavia Nomad Replicadispatches message to the remoteGovernanceRouterGovernanceRouterdispatched the message directly to the local recipient
Note on message recipient:
- the recipient may be a
ReplicaorHomecontract - it may be an
UpgradeBeaconthat controls the implementation ofReplicaorHome - it may be any other app
For simplicity & clarity to show the message flow, this diagram represents the recipient as a generic "App"
Specification
Glossary of Terms
- xApp - Cross-Chain Application
- role —
- an address stored in a smart contract's state that specifies an entity with special permissions on the contract
- permission to call certain functions is usually implemented using a function modifier that requires that the caller of the function is one of the roles with permission to call it; all contract calls sent from callers that do not have valid permission will revert
- example:
owneris the role set on all Ownable contracts upon deployment; theownerrole has exclusive permission to call functions with theonlyOwnermodifier
- permissioned function —
- any smart contract function that restricts callers of the function to a certain role or roles
- example: functions using the
onlyOwnermodifier on Ownable contracts
- permissioned call — a call to a permissioned function
- governor chain —
- the chain on which the
governoris deployed - the chain whose
GovernanceRouteris also the specialGovernorRouterwhich can send messages; allGovernanceRouterson other chains can only receive governance messages
- the chain on which the
On-Chain Components
GovernanceRouter
- xApp designed to perform permissioned roles on core Nomad contracts on all chains
- State Variables
- governor state variable
- if the
governoris local,governorwill be set to the EVM address of thegovernor - if the
governoris remote,governorwill beaddress(0)
- if the
- governorDomain state variable
- the Nomad domain of the governor chain
- stored as a state variable on all
GovernanceRouters; should be the same on allGovernanceRouters; always non-zero- if the
governoris local,governorDomainis equal to theoriginDomainof the localHomecontract - if the
governoris remote,governorDomainis equal to theoriginDomainof the remoteHomecontract
- if the
- equal to the
originDomainof the localHomecontract on the chain of theGovernorRouter - used by all
GovernanceRoutersto determine whether an incoming Nomad message was sent from theGovernorRouter- if the message is from the
GovernorRouter, theGovernanceRouterwill handle the incoming message - if not, it will revert
- if the message is from the
- routers state variable
- a mapping of domain → address of the remote
GovernanceRouteron every other chain
- a mapping of domain → address of the remote
- domains state variable
- an array of all domains that are registered in
routers - used to loop through and message all other chains when taking governance actions
- there is the possibility that some domains in the array are null (if a chain has been de-registered)
- an array of all domains that are registered in
- GovernorRouter
- the special
GovernanceRouterthat has permission to send governance messages to all otherGovernanceRouters - the
GovernanceRouteron the governor chain
- the special
Governor
- via the
GovernanceRoutersystem, it has the unique ability to call permissioned functions on any contract on any chain that transfers permission to the localGovernanceRouter - the role with permission to send messages to the
GovernorRouter- the
GovernorRouterhas exclusive permission to send messages via Nomad to all otherGovernanceRouters - the
GovernanceRouterscan have arbitrary permissions delegated to them by any contract on their local chain - therefore, the
governoris the entity with the power to call any permissioned function delegated to anyGovernanceRouteron any chain
- the
- there is only one
governorthroughout the Nomad system; it can be deployed on any chain - the
governorrole can always be transferred to another contract, on the same chain or a different remote chain - stored as a state variable on
GovernanceRouters; set to zero on allGovernanceRoutersexcept on the governor chain - Any contract on any chain that wishes for this governance system to have discretion to call a set of its functions can create a role & a function modifier giving exclusive permission to that role to call the function(s) (similar pattern to Ownable). The contract must then set the local
GovernanceRouterto the permissioned role, which — by extension — gives thegovernorexclusive permission to call those functions (regardless of whether thegovernoris remote or local)
Failure States
If there is fraud on the Nomad Home contract on the governor chain, this is currently a "catastrophic failure state" — no further governance actions can be rolled out to remote chains; we must create a plan to recover the system in this case.
Message Types
Executing (Arbitrary) Calls
- for each chain, the
governorconstructs the array of(to, data)calls to the permissioned functions on the contracts that will perform the upgrades on that chain - the
governorsends a transaction to theGovernanceRouter.callRemotefunction on its local the , passing in thedomainof the remote chain and the array of(to, data)calls of transactions to execute on that chain - the local
GovernanceRouterconstructs an Nomad-compatible message from the array of calls, addresses the message to the remoteGovernanceRouter, and sends the message to the localHomecontract - the message is relayed from the local
Hometo the remoteReplicacontract on the specifieddomain - the
Replicadispatches the message to the specified recipient, which is the localGovernanceRouter - the
GovernanceRouterparses the message to decode the array of(to, data)calls - the
GovernanceRouteruses low-level call to execute each of the transactions in the array within the local chain
Transferring Governor
Possible State Transitions
- called by the local owner to transfer ownership to another local owner (
domaindoes not change,ownerchanges to a newbytes32address) - called by the local owner to transfer ownership to a remote owner (
domainchanges to the remote,ownerchanges from a non-zerobytes32tobytes32(0)) - called by a remote owner to transfer ownership to a local owner (
domainchanges to the local domain,ownerchanges frombytes32(0)to a non-zerobytes32) - called by a remote owner to transfer ownership to another remote owner (
domainchanges to the new remote owner,ownerremainsbytes32(0))
Enrolling a Router
- used when a new chain is added to Nomad after we've already set up the system and transferred governorship
- add a new domain → address mapping to the
routersmapping on every otherGovernanceRouter
Functionality at Launch
Permissioned Roles
At launch, the GovernanceRouter system will have the following permissions:
- upgrade the implementation of
Home(viaUpgradeBeaconpattern) - upgrade the implementation of all
Replicas(via 1-to-NUpgradeBeaconpattern) - upgrade the implementation of itself (via
UpgradeBeaconpattern)
The GovernanceRouter will NOT have permission to:
- un-enroll a
Replicafrom theUsingNomadcontract, which will require a specialized role that can act quickly
Governor
The flexibility of this system will support a move to progressive decentralization.
Initially, the governor will most likely be a multisig controlled by trusted team and community members
Later, the governor role will most likely be transferred to a decentralized governance contract